mini-siem-elk
Integrate Winlogbeat with ELK Stack
This guide walks you through setting up Winlogbeat on a Windows 10 VM to collect Windows Event Logs and send them to your Logstash + Elasticsearch setup.
✅ Tested with Winlogbeat 9.0.0 and ELK Stack 8.17.4
🖥️ 1. Create a Separate Windows 10 VM
Before configuring Winlogbeat, create a dedicated Windows 10 virtual machine using VirtualBox, VMware, or any hypervisor.
🔹 Minimum requirements:
- 2 GB RAM
- 2 CPU cores
- Bridged or NAT Network (accessible to Ubuntu/ELK VM)
- Enable file sharing or internet access to download Winlogbeat
📦 2. Download and Extract Winlogbeat
- Download the
.zipversion of Winlogbeat. - Extract the contents (e.g.,
winlogbeat-9.0.0-windows-x86_64.zip) to:
C:\Users\<YourName>\Desktop\winlogbeat-9.0.0-windows-x86_64
⚙️ 3. Configure winlogbeat.yml
Edit the file winlogbeat.yml:
Enable Logstash Output
output.logstash:
hosts: ["192.168.1.10:5044"]
📌 Replace
192.168.1.10with the IP address of your Ubuntu/Logstash VM.
Disable Elasticsearch Output
# output.elasticsearch:
# hosts: ["localhost:9200"]
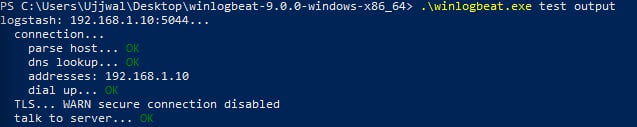
🔗 4. Test Connection to Logstash
Open PowerShell and navigate to the extracted folder:
.\winlogbeat.exe test output
✅ Output should show:
connection... OK
talk to server... OK
⚠️ Warning about TLS can be ignored for non-secure lab setups.
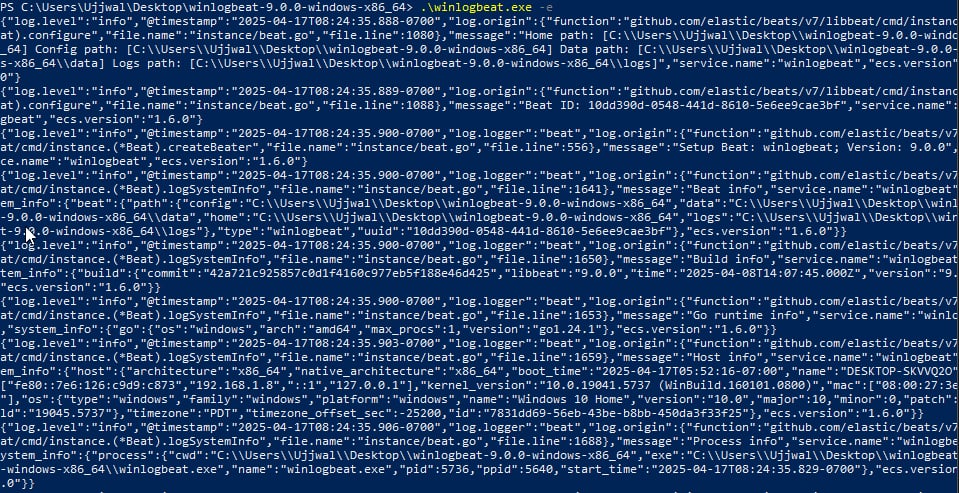
🚀 5. Run Winlogbeat
Run Winlogbeat in real-time to confirm event log transmission:
.\winlogbeat.exe -e
📤 Logs will begin to flow to Logstash if everything is working.
🔧 6. Update logstash.conf on ELK Server
Ensure your Logstash config can accept Winlogbeat logs.
input {
beats {
port => 5044
}
}
filter {
if "winlogbeat" in [agent][name] {
mutate {
add_field => { "source_type" => "windows_event_log" }
}
}
}
output {
if "winlogbeat" in [agent][name] {
elasticsearch {
hosts => ["https://localhost:9200"]
user => "elastic"
password => "your_password"
ssl_enabled => true
ssl_verification_mode => "full"
ssl_certificate_authorities => ["/path/to/http_ca.crt"]
index => "winlogbeat-events"
}
stdout { codec => rubydebug }
}
}
🔁 Restart Logstash to apply changes.
📊 7. Visualize Windows Logs in Kibana
- Go to Kibana > Stack Management > Data Views
- Create a new Data View:
Pattern: winlogbeat-events
- Go to Discover and select your new Data View to inspect logs.
🗂️ Screenshot Directory
All referenced images should be stored in:
/images/05-integrate-winlogbeat